Manage your
devices smarter
Miradore has all the right features for effective Android, Apple, and Windows device management in a single platform. It’s easy to use and you can get started in minutes!

Trusted by over 10,000 companies in more than 180 countries
Award-winning
Mobile device management solution
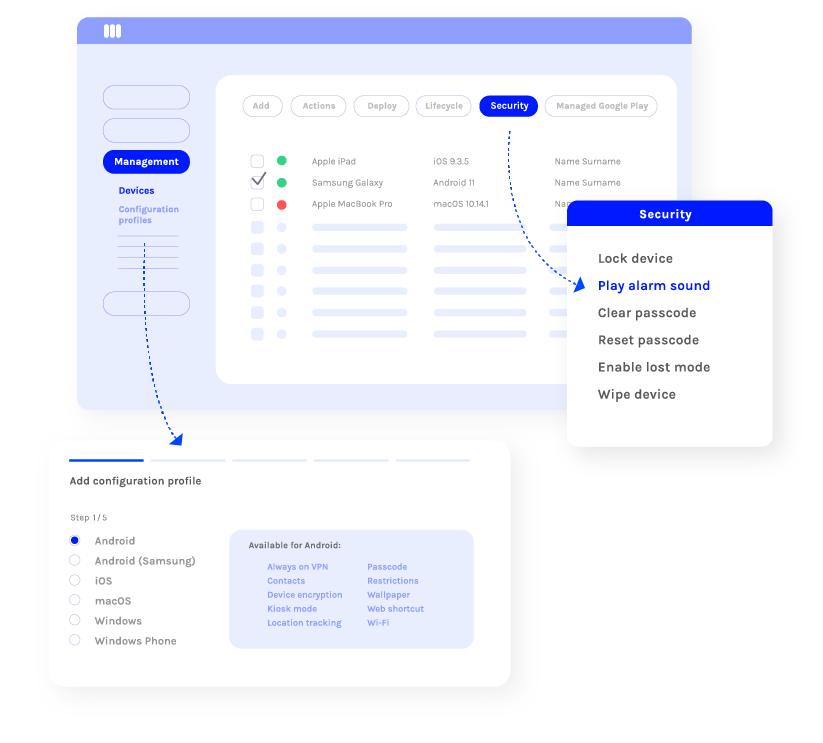
Secure your devices and data
Miradore helps to ensure device and data security as well as data compliance across the organization. You can easily encrypt all confidential data, separate business and personal use, enforce safe passcodes and screen locks, and prevent the use of unwanted applications.
Control your device fleet
With Miradore, you’ll have total control over the use of devices in your organization. You can install device configurations remotely, manage the use of applications, and access dashboards and reports.

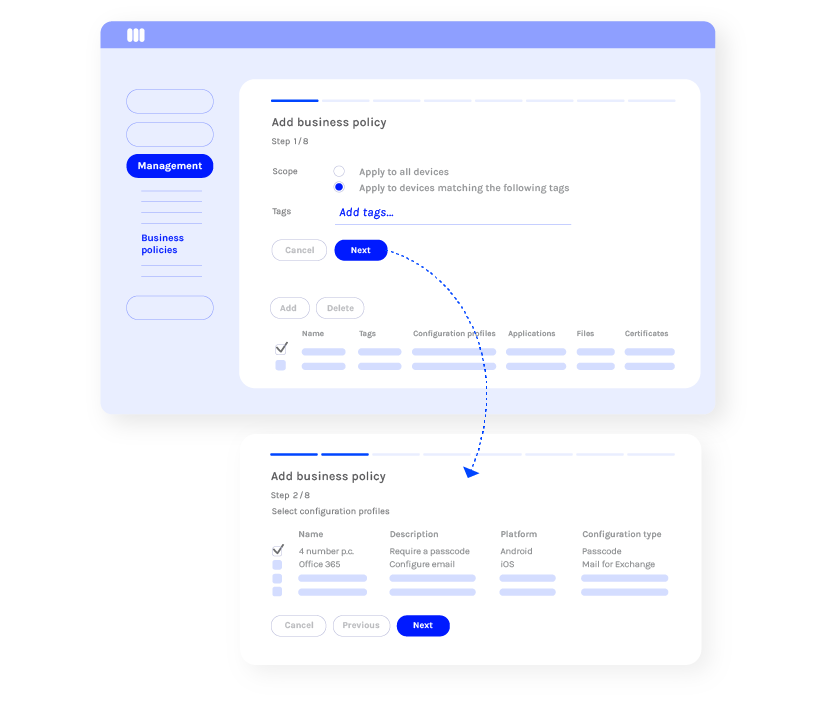
Save time by automating tasks
Miradore’s automation capabilities, such as Business Policies, enable you to work more efficiently as you can enroll and configure devices faster. Disposing manual tasks will reduce human errors and help ensure compliance and secure use of mobile devices.

“Miradore has dramatically increased the ease with which we manage our devices – the interface is intuitive and extremely simple to navigate.”
Billington Food Service









