Platforms
Android Device Management (Android MDM)
Miradore enables mobile device management across all Android device manufacturers. It helps you set up devices with ease, secure both data and devices, and manage Android settings and applications remotely.
Miradore supports Android smartphones and tablets running 6.0 and newer.
Key features for Android
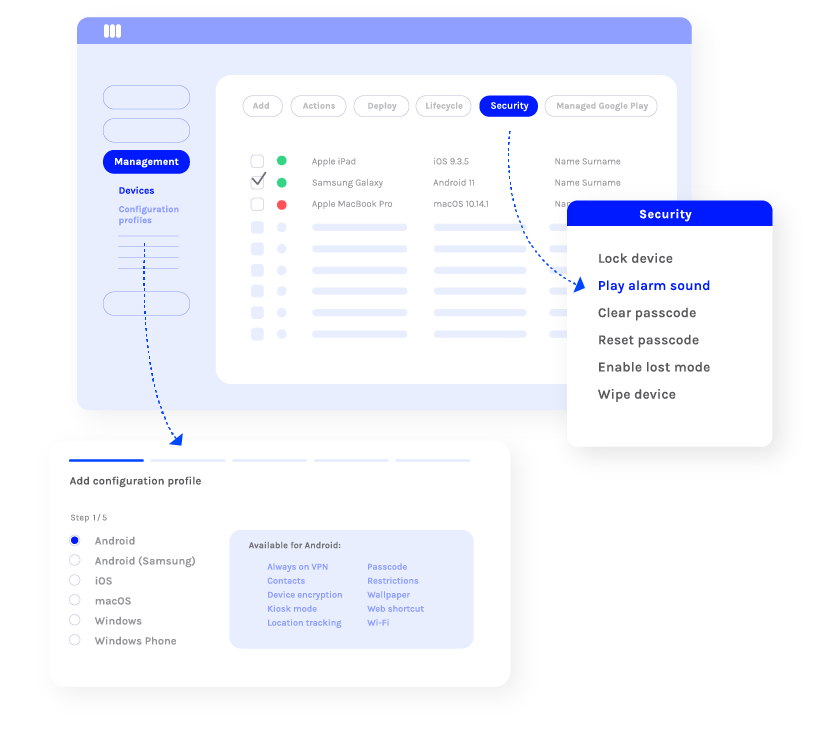
Secure your Android devices and company data
Miradore’s various security features enable you to keep your devices and data safe.
-
- enforce a passcode
- lock and wipe a device
- reset/clear the passcode
- play an alarm sound
- track device location
-
- separate business data from personal data with secure containers
- encrypt mobile device storage
- manage Android system updates
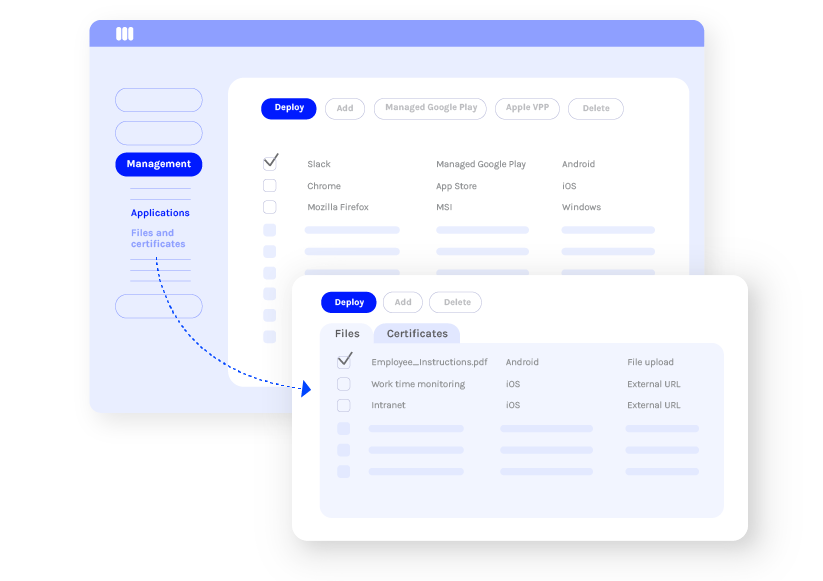
Provide your employees with all the right tools to work productively
Miradore’s app and content management capabilities allow you to deploy all the necessary applications, files, and contacts remotely to your employees’ Android devices.
- deploy, update, and remove applications, files, and contacts
- deploy certificates
- whitelist and blacklist applications
- create web shortcuts
Applications can be managed securely through the Managed Google Play Store, an enterprise version of Google Play Store.
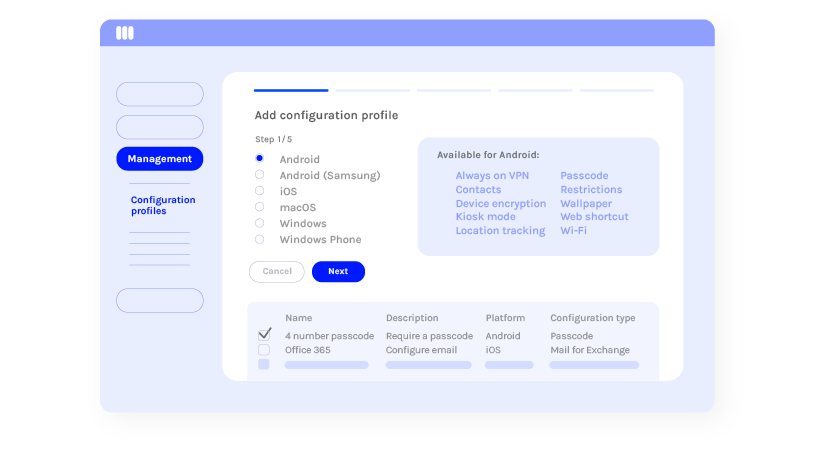
Set the right configurations for each device
Make it easier for your employees to take new devices into use by pre-configuring device settings while saving both your employees’ and IT administrator’s time.
- configure email, Wi-Fi, VPN, and managed accounts (e.g. Outlook)
- enforce a password
- set a custom wallpaper
- limit system applications (e.g. camera)
Take charge of your organization’s device usage
Set various restrictions for your Android devices to ensure that devices are always used correctly and safely.
- turn devices into Kiosk mode
- limit data roaming
- blacklist applications
- deny access to Google Play Store
- deny screen capture
- deny factory reset

Bring clarity to your device fleet
With Miradore, you can quickly get a view of your entire device inventory and device users. You can access essential information on both hardware and software, including installed applications, device security status, and network data usage.
- dashboard widgets
- standard and custom reports
- device inventory data

Manage multiple Android devices more efficiently
Automating device management helps you save time and money and reduce human errors.
Automate device enrollment
Miradore supports Android Zero-Touch Enrollment and Samsung Knox for device enrollment.
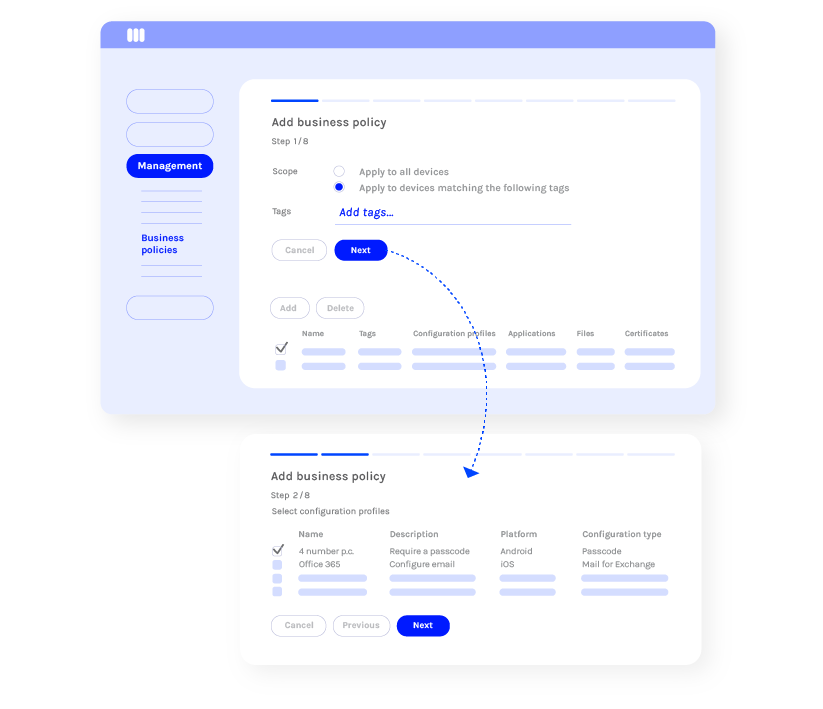
Automate device configurations
Automate the deployment of various configurations, restrictions, applications, and files with Miradore’s Business Policies.
Business Policies are collections of applications and configurations that can be automatically deployed to devices based on device and user groups.
Supported Android device management tools
Android Enterprise
Android Enterprise (previously known as Android for Work) is Google’s platform for Android device management. It is a set of device management APIs and tools built into the Android operating system that enables extensive security and management features for Android 6.0 or newer.
Android Enterprise unifies Android management by removing device manufacturer variations and offers the same management features for all Android devices.
Miradore is an official Google Partner for Enterprise Mobility Management.
Managed Google Play Store
Managed Google Play Store is an enterprise version of Google Play Store and it gives more control over application usage. With Miradore, you can easily create a Managed Google Play Store for your organization.
Once set up, you can deploy applications to devices through the Managed Google Play Store or allow users to download approved applications on their own by giving access to your app store.
Furthermore, you can manage application rights and licenses in Managed Google Play Store, which increases transparency and security.
Android Zero-Touch Enrollment
Android Zero-Touch Enrollment (ZTE) is an Android feature that can be used to automate the setup of company-owned devices.
With ZTE, the device user only needs to turn on or reset a device, and the device provisions itself with the enterprise apps and settings.
Samsung Knox
Samsung Knox is a mobile security platform that comes preinstalled on most Samsung smartphones and tablets.
The Knox-enabled Samsung devices have built-in support for many additional security features, which enables you to control and secure the devices effectively with a management solution.
Choose the right management methods for your devices
Work profile
Great for personal (BYOD) devices
Work profile (also known as Profile owner) mode enables you to secure company data on a personal (employee-owned) device without risking the user’s privacy. The work profile is a container, which isolates work data and apps from personal use on an Android device.
This management method is the best choice for Bring-Your-Own-Device (BYOD) scenarios where employees or contractors use their personal devices for working and accessing your organization’s resources.
Fully managed device
The preferred method for company-owned devices
Fully managed device (also known as Device owner) mode is the best option for managing devices owned by your organization.
Compared to the work profile, this management method gives IT admins more control over device settings, making it easier to ensure device and data security.
Fully managed with work profile
For company-owned devices used for both work and private use
Fully managed with work profile mode (also known as Android COPE) is the best option for managing devices that are owned by your organization and used for both work and private use.
This mode gives companies and device users all the benefits of the work profile mode with an added layer of security. IT can enforce a wide range of company policies on the entire device while device users can rest assured that their personal data, like installed applications, stays private.
Remote support for Android devices
When you need to provide mobile device support for your device users, you can quickly start a secure, attended session directly from Miradore.
Miradore offers remote support through our native integration with GoTo Resolve or TeamViewer integration (TeamViewer license required).

Billington Food Service transitions to Android using MDM from Miradore
Billington Food Service, a bespoke supplier to the UK’s food service industry, needed a new MDM solution as they transitioned from iOS to Android.
“Miradore has dramatically increased the ease with which we manage our devices – the interface is intuitive and extremely simple to navigate.”
Looking for technical details?
Knowledge Base
Browse our documentation and technical “how-to” articles on Android management.
Instructional videos
Watch our short tutorial videos to learn how to manage Android devices with Miradore.